As organizations increasingly turn to cloud storage solutions, the question of data security has become paramount. For law enforcement and prosecutors, safeguarding sensitive information is not just a best practice; it’s a necessity. Understanding the best cloud storage for law enforcement and prosecutors is critical to ensuring that data remains secure and accessible. This article examines the challenges to data security in the cloud, highlighting the inherent vulnerabilities and complexities, as well as the measures required to protect data efficiently.
What are the issues of storing data in the cloud?
Storing data in the cloud presents several cloud storage challenges that organizations must navigate. One of the primary issues is the inherent vulnerabilities of cloud storage systems, which can expose sensitive data to various threats.
Cybercriminals often target cloud systems to gain unauthorized access to sensitive information. This can result in data breaches that compromise personal and organizational data. According to Check Point Software, misconfigurations remain the #1 threat, with public buckets, permissive IAM roles, and unencrypted data opening doors for attackers.
Even with robust security measures, no system is entirely immune to breaches. The consequences can be severe, resulting in legal repercussions and a loss of public trust. In 2024, a considerable data breach exposed sensitive information from over 100 organizations, highlighting the critical need for enhanced security measures.
These threats underscore the importance of understanding the landscape of data privacy in cloud computing to implement efficient security measures. Additionally, using cloud solutions specifically designed for law enforcement, such as iCrimeFighter, ensures that data is managed by professionals who understand the unique challenges faced by these agencies.
What are the challenges faced when storing data in the cloud?
The complexities involved in data encryption and access management pose meaningful challenges when storing data in the cloud:
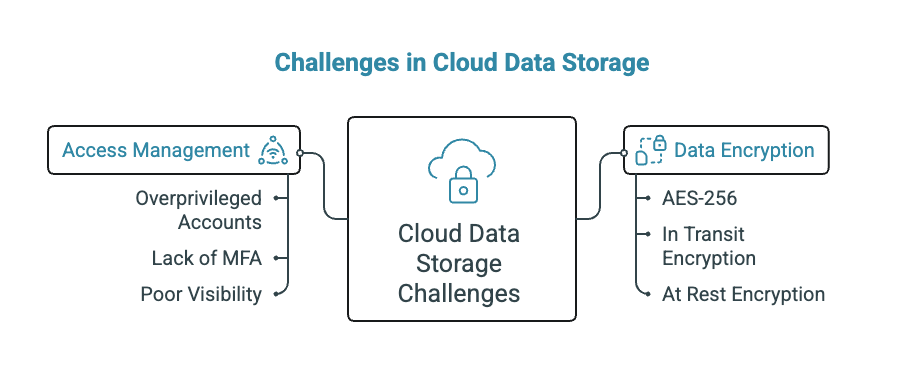
- Data Encryption: While encryption is a critical security measure, its implementation can be complex. Ensuring that data is encrypted both in transit and at rest requires a comprehensive understanding of the technology. Implementing strong encryption protocols like AES-256 helps keep sensitive information safe from unauthorized access, even if someone manages to intercept it.
- Access Management: Determining who has access to sensitive data can be challenging, especially in collaborative environments. Misconfigured access settings can lead to unauthorized data exposure. According to Check Point Software, IAM weaknesses fuel breaches, with overprivileged accounts, lack of MFA, and poor visibility into lateral movement enabling attackers to abuse access and escalate privileges.
Understanding the risks associated with storing sensitive data on cloud services is essential, as these risks are heightened for organizations like law enforcement, where data sensitivity is paramount. Solutions like iCrimeFighter offer unlimited cloud storage, ensuring that agencies can scale their data needs without compromising security.
What security measures are in place to protect data?
To mitigate the challenges of data security in the cloud, various security protocols are in place. These include:
- Encryption Encrypting data ensures that even if unauthorized users gain access, they cannot read the information without the decryption key. Implementing strong encryption protocols like AES-256 helps keep sensitive information safe from unauthorized access, even if someone manages to intercept it.
- Multi-factor authentication (MFA) MFA adds a layer of security by requiring users to provide multiple forms of verification before accessing sensitive data. Encouragingly, adoption of phishing-resistant authentication is rising, with 60% now using biometrics and 47% adopting passwordless passkey solutions. (cio.com)
| Compliance Standard | Infrastructure Platform |
|---|---|
| CJIS, SOC II, HIPAA, FIPS | AWS GovCloud (via iCrimeFighter) |
Compliance with standards and regulations also plays a vital role in safeguarding cloud data. Organizations must adhere to laws such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) to ensure data privacy in cloud computing. iCrimeFighter is built to meet full compliance with standards like CJIS, SOC II, HIPAA, and FIPS via AWS GovCloud, providing peace of mind for law enforcement agencies.
What are some challenges investigators may encounter with data that is stored in the cloud?
When it comes to investigations, cloud storage can introduce unique challenges that complicate data retrieval and the chain of custody:
Accessing data stored in the cloud may require navigating through various service providers, each with its own policies and protocols. In 2024, a meaningful data breach exposed sensitive information from over 100 organizations, highlighting the critical need for enhanced security measures.
Maintaining a clear chain of custody is vital for legal proceedings. Cloud storage can complicate this process, as data may be stored across multiple jurisdictions. In 2024, a meaningful data breach exposed sensitive information from over 100 organizations, highlighting the critical need for enhanced security measures.
Additionally, challenges that cloud storage poses for data security include jurisdictional issues and data ownership challenges, which can hinder investigations and legal processes. However, solutions like iCrimeFighter enable one-click sharing with prosecutors and other agencies, eliminating the need for physical media like DVDs or CDs, thereby streamlining the process and enhancing collaboration.

.png)