Navigating Cloud Forensics
As law enforcement and prosecutors increasingly rely on digital evidence, the role of cloud forensics has become paramount. Understanding the complexities and challenges associated with this field is essential for effective digital investigations. In this article, we will explore the main challenges in cloud forensics, shedding light on its significance and the hurdles faced by forensic analysts in the cloud environment.
What is cloud forensics?
Cloud forensics refers to the application of forensic science to cloud computing environments. It plays a crucial role in digital investigations by enabling the collection, preservation, analysis, and presentation of data stored in the cloud. Unlike traditional forensics, which often involves physical devices, cloud forensics deals with data that is distributed across various servers and locations, making it more complex.
Differences between traditional forensics and cloud forensics:
| Feature | Traditional Forensics | Cloud Forensics |
|---|---|---|
| Data Location | Typically focuses on data stored on local devices. | Involves data that may reside on servers operated by third-party providers. |
| Access Challenges | More straightforward access methods. | Requires navigating through multiple layers of security and compliance protocols. |
| Data Ownership | Ownership is usually clear (device owner). | Questions of ownership and jurisdiction can complicate investigations; data may belong to different entities. |
Understanding these distinctions is vital for forensic analysts as they navigate the landscape of digital investigations.
What are the challenges of cloud forensics?
The cloud forensics challenges are numerous and complex. Here are some key issues that forensic analysts face:
Data Access: Gaining access to cloud data can be challenging due to strict security measures. According to Help Net Security, 34% of organizations report limited cybersecurity skills specific to cloud technologies. (helpnetsecurity.com)
Jurisdiction Issues: Data may be subject to laws from multiple jurisdictions. The Cloud Security Alliance highlights that 23% of cloud alerts are never investigated due to jurisdictional complexities. (cloudsecurityalliance.org)
Provider Cooperation
Cooperation from cloud service providers is often necessary. NIST emphasizes the need for collaboration between service providers and forensic experts. (nist.gov)
Shared Environments: 65% of organizations spend 3-5 days longer investigating incidents in the cloud compared to on-premises due to multi-tenant challenges. (cloudsecurityalliance.org)
How do data privacy regulations impact forensic investigations in the cloud?
Data privacy regulations, such as GDPR and HIPAA, impose strict guidelines on how personal data must be handled. These regulations can complicate forensic investigations in several ways:
- Data Access Restrictions: Analysts may face legal barriers to accessing certain data. A study by Encryption Consulting indicates that 42% of U.S. states have passed consumer privacy statutes as of 2025. (encryptionconsulting.com)
- Compliance Challenges: Forensic analysts must ensure methods comply with relevant regulations. The Cloud Security Alliance reports that 23% of cloud alerts are never investigated due to compliance challenges. (cloudsecurityalliance.org)
- Legal Ramifications: Failure to adhere to laws can result in significant legal consequences. NIST emphasizes the need for compliance with legal frameworks to avoid legal ramifications. (nist.gov)

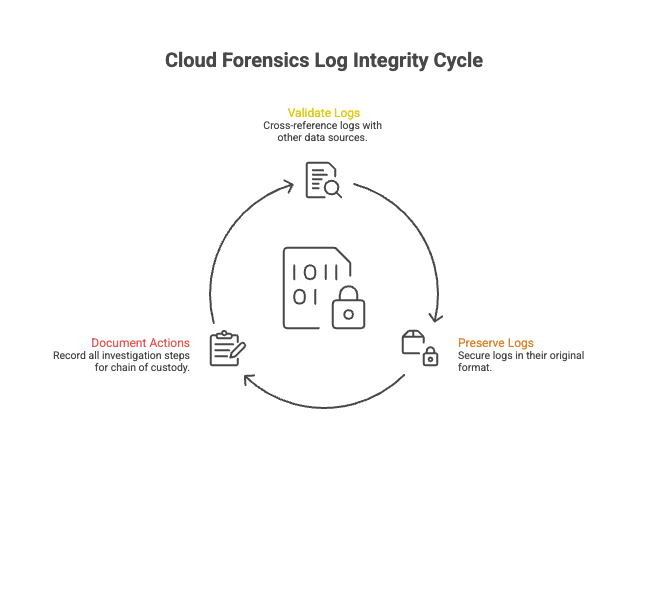
How can forensic analysts ensure the integrity of access logs collected from a cloud provider during an investigation?
Ensuring the integrity of access logs is critical in the cloud forensics process. Here are some best practices for forensic analysts:
Validation
Verify the authenticity of the logs by cross-referencing them with other sources of data.
Preservation
Use secure methods to preserve logs in their original format to prevent tampering.
Documentation
Maintain detailed records of all actions taken during the investigation to establish a clear chain of custody.
Tools and techniques for log integrity
- Hashing: Utilize cryptographic hashing to create a unique fingerprint of the logs, ensuring they remain unchanged.
- Access Control: Implement strict access controls to limit who can view or modify logs.
- Regular Audits: Conduct periodic audits of log data to detect any discrepancies or unauthorized access.
These practices help maintain the integrity of logs, which is crucial for substantiating findings in court.
What is the process of cloud forensics?
The cloud forensics process involves several critical steps to ensure a thorough investigation:
- Identification: Determine the scope of the investigation and identify relevant data sources.
- Collection: Gather data from cloud environments while adhering to legal and compliance requirements.
- Preservation: Secure the collected data to prevent alteration or loss.
- Analysis: Analyze the data to uncover relevant evidence.
- Presentation: Prepare findings clearly and concisely for legal proceedings.
Importance of cloud forensics certification
Obtaining a cloud forensics certification can enhance an analyst's competency and credibility. This certification ensures that professionals are equipped with the necessary skills and knowledge to navigate the complexities of cloud forensics effectively.
In conclusion, the challenges in cloud forensics are multifaceted and require a nuanced understanding of technology, law, and investigative techniques. As the landscape of digital evidence evolves, so too must the approaches employed by law enforcement and prosecutors.
Modernize Your Digital Evidence Management
To address these challenges, agencies can leverage solutions specifically designed for law enforcement, such as iCrimeFighter, which enables agencies to start operations in less than a day.
Moreover, with unlimited cloud storage, agencies can securely store vast amounts of data while ensuring full compliance with standards such as CJIS, SOC II, HIPAA, and FIPS via AWS GovCloud. This scalability allows law enforcement to adapt to evolving data needs without compromising security or compliance.
Discover how cloud storage can revolutionize the way law enforcement and prosecutors manage critical data, enhancing collaboration and security.
Contact us to transform your agency

.png)