In an era where digital evidence is pivotal in criminal investigations, understanding the legal procedures for accessing cloud data is crucial for law enforcement and prosecutors. As more data is stored in the cloud, ensuring lawful access becomes not only a legal requirement but also a matter of ethical responsibility. This article explores the specific legal procedures investigators must follow, the frameworks protecting proprietary data, and the documentation required to access cloud-stored evidence.
What is lawful access to cloud data?
Lawful access refers to the legal authority that investigators must possess to access data stored in the cloud. This concept is vital because it ensures that investigators operate within the bounds of the law, maintaining the integrity of the evidence collected. The implications of the Lawful Access to Encrypted Data Act are significant; it aims to clarify the legal pathways for accessing encrypted data, thereby enhancing law enforcement's ability to investigate crimes while balancing individuals' privacy rights.
Understanding what constitutes lawful access is essential for investigators, as it helps them navigate the complexities of digital evidence collection while adhering to legal standards. Additionally, utilizing cloud storage solutions built specifically for law enforcement can streamline this process. With features like one-click sharing with prosecutors and other agencies, investigators can efficiently comply with legal requirements while ensuring that evidence is securely stored and easily accessible.
What legal frameworks protect proprietary data in criminal cases?
Several legal frameworks govern the protection of proprietary information, particularly in the context of cloud data. Key among these is the Electronic Communications Privacy Act (ECPA), which stipulates how government access to encrypted communications can be obtained. This act is crucial for investigators, as it outlines the conditions under which they can legally access electronic communications and stored data.
Additionally, the Fourth Amendment provides constitutional protection against unreasonable searches and seizures, further complicating the legal landscape. Investigators must be well-versed in these frameworks to ensure they do not inadvertently violate privacy rights while seeking necessary evidence.
Compliance Standards & Security
Furthermore, using cloud storage solutions that ensure full compliance with regulations such as CJIS, SOC II, HIPAA, and FIPS via AWS GovCloud can help mitigate legal risks associated with accessing sensitive data.
What legal documentation must investigators obtain before accessing cloud-stored evidence?
Before accessing cloud data, investigators must secure specific legal documentation to ensure compliance with applicable laws. The primary documents include:
Search Warrants
Required to access data stored in the cloud and must be issued by a judge based on probable cause.
Subpoenas
May be used to compel cloud service providers to release data, particularly in cases where a warrant may not be necessary.
Court Orders
In certain situations, investigators may need a court order to access specific types of data.
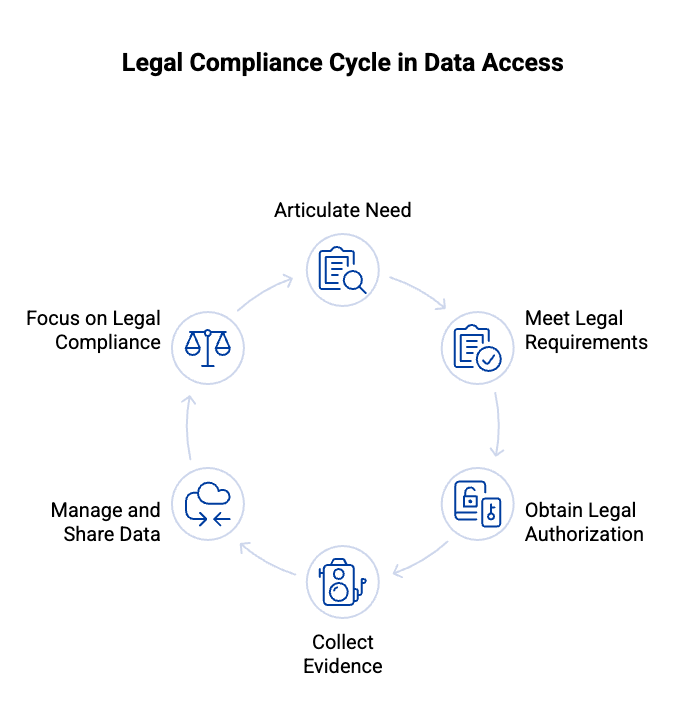
The process of obtaining these documents can be challenging, as investigators must clearly articulate their need for access and ensure that they meet all legal requirements. Understanding whether investigators need legal authorization to access the data is crucial; without it, any evidence collected may be deemed inadmissible in court. Utilizing platforms like iCrimeFighter, which can be operational in less than a day, can expedite the process of data management and sharing, allowing investigators to focus on legal compliance.
What legal considerations should be taken into account when conducting forensic data recovery?
When conducting forensic data recovery, investigators must consider several legal factors to ensure compliance with laws and regulations. Key considerations include:
- Adherence to the Lawful Access to Encrypted Data Act: Investigators should be aware of whether this act has passed and its implications for accessing encrypted data.
- Chain of Custody: Maintaining a clear and documented chain of custody is essential for the admissibility of evidence in court. Any breach could lead to challenges regarding the integrity of the data.
- Privacy Rights: Investigators must strike a balance between the need for data access and the privacy rights of individuals, ensuring that they do not infringe upon constitutional protections.
These considerations are paramount in ensuring that forensic recovery efforts are both effective and legally sound. Leveraging cloud storage solutions designed for law enforcement can further enhance the integrity of the data and help maintain compliance with legal standards.

How do courts decide whether to disclose proprietary information during a trial?
Courts use specific criteria to determine whether to disclose proprietary information during a trial. Factors include:
| Factor | Description |
|---|---|
| Public Interest | Courts often weigh the public's right to know against the proprietary rights of the data holder. If the public interest is deemed significant, courts may lean towards disclosure. |
| Relevance to the Case | The information must be relevant to the proceedings. If it contributes directly to the case's outcome, courts are more likely to allow its disclosure. |
| Potential Harm | Courts also consider whether disclosing the information could cause harm to the proprietary rights of the data holder or to third parties. |
Striking a balance between public interest and proprietary rights is a delicate task for courts, and understanding these criteria is essential for investigators involved in legal proceedings. By utilizing cloud storage solutions that offer unlimited storage, investigators can ensure that all relevant data is securely stored and readily available for legal review.

